 UPDATE: VALIDATED THIS PROCESS ON WINDOWS 10 1909 – SEPT 18 2020
UPDATE: VALIDATED THIS PROCESS ON WINDOWS 10 1909 – SEPT 18 2020
If you have Windows 10 clients on a WSUS server and you want to confirm that they are receiving patches from that WSUS server and not going directly to Microsoft to update, you used to just read the %SystemRoot%\WindowsUpdate.log. Under Windows 10 however, that log now looks like:
Windows Update logs are now generated using ETW (Event Tracing for Windows).
Please run the Get-WindowsUpdateLog PowerShell command to convert ETW traces into a readable WindowsUpdate.log.
For more information, please visit http://go.microsoft.com/fwlink/?LinkId=518345
 This is quite frustrating because it is the only way to easily confirm that your clients are taking updates from WSUS. The really good news is that when you run the command they suggest to build a log, it requires a “symbols” to be installed which is just another big pain in the butt. To get around this I found a blog that suggested the following command in POWERSHELL (ADMIN):
This is quite frustrating because it is the only way to easily confirm that your clients are taking updates from WSUS. The really good news is that when you run the command they suggest to build a log, it requires a “symbols” to be installed which is just another big pain in the butt. To get around this I found a blog that suggested the following command in POWERSHELL (ADMIN):
wuauclt /detectnow
Get-WindowsUpdateLog -SymbolServer https://msdl.microsoft.com/download/symbols -LogPath C:\windowsupdate.log
UPDATE: Oct 13, 2016: Microsoft Partner Support tells me that at least on Windows 10, specifying the SYMBOL SERVER is not required as it will automatically pull down any missing symbols without the switch so you can use:
wuauclt /detectnow
Get-WindowsUpdateLog -LogPath C:\windowsupdate.log
I have tested this and found it definitely works on Windows 10 1607.
If you want to run this on a remote machine use:
Get-WindowsUpdateLog -ETLPath \\<HOSTNAME>\C$\windows\Logs\WindowsUpdate -SymbolServer https://msdl.microsoft.com/download/symbols -LogPath C:\LOGS\windowsupdate_<HOSTNAME>.log
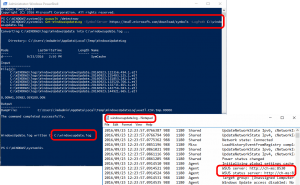
You can then open the log with notepad and look for “WSUS” like:
…
2016-09-22 15:08:04.9264690 724 25384 Agent WSUS server: http://ch-ms:8530
2016-09-22 15:08:04.9264694 724 25384 Agent WSUS status server: http://ch-ms:8530
2016-09-22 15:08:04.9264697 724 25384 Agent Target group: (Unassigned Computers)
…or the URL of your WSUS Server like:
…
2016-09-22 15:08:05.9325837 724 24984 ProtocolTalker ServiceId = {3DA21691-E39D-4DA6-8A4B-B43877BCBB7}, Server URL = http://ch-ms:8530/ClientWebService/client.asmx
…
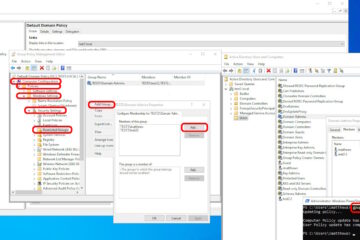
If you want to look further into your Windows 10 client’s you can check the registry to see what it:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate
but that is only a confirmation that your Windows 10 PC received the registry entries from your GPO… not that it is paying attention to that GPO. For instance, I am currently troubleshooting all my customers Windows 10 Enterprise 1607 Anniversary PC’s that have the GPO applied (according to GPRESULT /R) and the correct registry entry but NOT taking updates from WSUS. When I find an answer, I will post it here.
10 Comments
Rose B · August 31, 2020 at 3:05 pm
This worked for me in build 1909, however, I don’t see a date/time stamp in the log file. Did this change or am I missing something?
Ian Matthews · September 18, 2020 at 11:28 am
Hi Rose;
I just ran the two lines in PowerShell again:
wuauclt /detectnow
Get-WindowsUpdateLog -LogPath C:\windowsupdate.log
and found that the log did show the date and time:
…
2020-09-17 17:25:27.5260937 77112 87432 Agent Initializing global settings cache
2020-09-17 17:25:27.5260947 77112 87432 Agent WSUS server: http://cal-mss2:8530
2020-09-17 17:25:27.5260957 77112 87432 Agent WSUS status server: http://cal-mss2:8530
2020-09-17 17:25:27.5260965 77112 87432 Agent Alternate Download Server: (null)
…
Can you post a sample of what your log looked like?
nooboffduty · July 24, 2019 at 1:02 pm
Thanks for this!
Joe · June 27, 2017 at 8:23 am
Hello,
At the end there you said you would post the answer when you find it.
Did you ever find it? Or is it posted somewhere else?
Thanks,
Joe
Ian Matthews · July 4, 2017 at 2:30 pm
Sorry Joe, I did not find anymore useful information on the source of Windows Updates.
Roman · May 26, 2017 at 9:04 am
In cmd.exe (or even in powershell.exe) type:
findstr “WSUS server:” c:\windows\WindowsUpdate.log
This will give you output similar to:
2016-11-09 09:39:45:820 872 a8c AU # WSUS server: http://wsus-XX:8530
2016-11-11 04:02:41:404 852 53c Agent * WSUS server: http://wsus-XX:8530
That’s your WSUS server.
Cheers,
—Roman
Jon · January 17, 2017 at 4:18 am
Hi, Thanks for posting this – couldn’t find the info anywhere else. Unfortunately when I generate the log files they have no info in them about the source of the updates (no ‘Agent’ tags, URL etc) . I have 1607. Am I missing something? Thanks, Jon
Ian Matthews · January 18, 2017 at 7:58 pm
Hi Jon;
I have run that command on 1511 and 1607 and both produced the results shown in post. Have you searched for the name of your WSUS server in the logs?
Jon · January 19, 2017 at 2:43 am
Hi Ian, Thanks for your reply. No sign of anything to do with the WSUS server in the log files, even though I now know that it is at last going to the WSUS server for updates.
SOLVED: Window 10 1607 Not Applying GPO’s For Windows Update - Up & Running Technologies Calgary · October 14, 2016 at 8:17 am
[…] Worse, the Windows Update log shows it cannot talk to the WSUS server: If you want to read your Windows 10 Windows Update Log, we have the process detailed HERE. […]